[ CleverThings.com ] [ Company Policies ] → Security Policy
Our Security Policies
Security Precautions
Security Breach Procedures
Certificates for Secure Web Browsing - HTTPS / SSL
Company Security Practices
Security Precautions
All of our forms that collect sensitive data utilize high-grade Secure Socket Layer (SSL) (AES-128 / 128-bit) encryption to ensure the security and integrity of your transmitted information. SSL is the preferred method of secure communication, and can be identified by the secure page being preceded by HTTPS:// in your web browser address bar. Many web browsers will also show the certificate owner in a blue or green box on the address bar.

Most web browsers will display a locked padlock icon next to the URL or in the bottom right corner of the browser whenever your communication is secure.
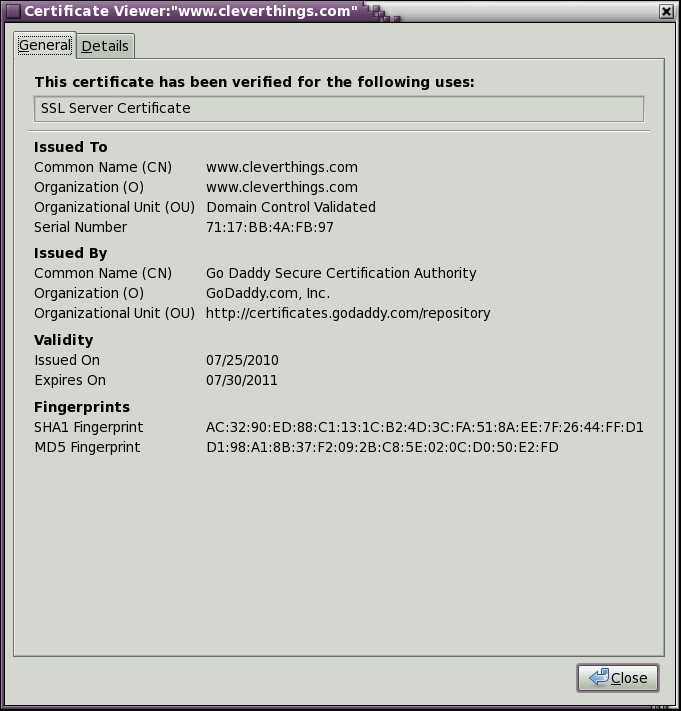
If you click on the locked padlock icon, the secure certificate will be displayed. We recommend that you always read and verify the security certificate information the first time you visit a web site, and be sure that this information matches the company that operates the web site.
If you prefer to not make credit card purchases over the Internet, we give you the option to pay by telephone or postal mail. You may use our web site to select all of your items on your shopping list, then choose the "Pay by Phone" or any of the other convenient options during the payment checkout process. (Sorry, no CODs!)
Security Breach Procedures
It is important that we have complete contact information for all of our customers so they can be immediately notified of any security incident. Our employees make every effort to always remain vigilant and maintain a high level of security at all times. Our corporate security policies go above and beyond the legal requirements for the payment card industry.
We carefully screen all of our employees (including call center representatives) with thorough background checks and random drug testing. Our employees know how to identify possible security breaches, and they have been extensively trained in mitigating security risks. Refresher training and audits are performed on a quarterly basis.
Certificates for Secure Web Browsing - HTTPS / SSL
To protect your sensitive data, we use a form of data encryption that requires your web browser to exchange a security "certificate" with our server. If your web browser gives you a warning message regarding a security certificate, ALWAYS VIEW THE CERTIFICATE before you accept the connection!
Company Security Practices
Physical Security is the first step in protecting data. Without good physical security, no other security practices can be effective. We use a world-class data center, and access to our cloud and corporate data centers is strictly limited and all of our employees have been issued a photo identification card.
Technical Security is the second step in data protection. All of our data is encrypted as it is stored on disk. All computers and hard disks are protected with strong password authentication. This combination ensures that the data can't be accessed if there is ever a breach in physical security. The integrity of our file systems is monitored and all of our data is backed up to allow rapid restoration after a hardware failure.
Administrative Security is the last step in keeping data secure. It begins with a careful selection of employees while maintaining up-to-date access control lists. We have a thorough training program for new employees and only the minimum of access privileges are granted.
To further prevent the loss, misuse, or disclosure of your personal information, all of our employees are required to sign a strict Non-Disclosure Agreement (NDA).
This policy was last revised on Saturday, October 23rd, 2021.